On 15 March. 2001, a Linux honeypot
was successfully compromised, a rootkit was download to the / partition
and then deleted from the system. Your mission is to find and recover the deleted rootkit.
If you are not sure where to begin on conducting this forensic analysis
and recover the rootkit, we highly reccommend you start with the Forensic Challenge.
The steps you will have to follow for the rootkit recovery are similar
to the steps discussed there. We have posted only the / partion for
download to keep this challenge simple. The compressed image is 13MB, (honeynet.tar.gz) MD5=0dff8fb9fe022ea80d8f1a4e4ae33e21.
Once you have downloaded, untarred, and unzipped the partition image,
it will be 255 MB and the checksum should be
MD5=5a8ebf5725b15e563c825be85f2f852e.
- Show step by step how you identify and recover the deleted rootkit from the / partition.
- What files make up the deleted rootkit?
Bonus Question:
Was the rootkit ever actually installed on the system? How do you know?
Was the rootkit ever actually installed on the system? How do you know?
Source: http://old.honeynet.org/scans/scan15/
Lets start.
Open up terminal and type
sudo apt-get update
then copy the download link from honeynet or just download it from there. However I used
wget http://old.honeynet.org/scans/scan15/honeynet.tar.gz
I downloaded it in to my home folder and then untarred it with
tar -xvf honeynet.tar.gz
where -x = Extract files from an archive
-v = verbosely list files processed
-f = use archive file or device archive
SUMMARY
-------
You have download the / partition of a compromised RH 6.2
Linux box. Your mission is to recover the deleted rootkit
from the / partition.
What is rootkit actually ?
From Wikipedia: " rootkit is a stealthy type of software, often malicious, designed to hide the existence of certain processes or programs from normal methods of detection and enable continued privileged access to a computer"
So basically rootkit is not a virus which sabotages your computer. Its basic idea is to hide itself from users and give root access to someone else who then can steal your documents or somehow make changes to the system. It is a "kit" which contain files to give "root" access to the marauder.
then I downloaded autopsy to do the forensics
sudo apt-get install autopsy
What is autopsy ?
http://www.sleuthkit.org/
"Autopsy™ is a digital forensics platform and graphical interface to The Sleuth Kit™ and other digital forensics tools. It can be used by law enforcement, military, and corporate examiners to investigate what happened on a computer. You can even use it to recover photos from your camera's memory card."
This is what I have so far done. Now lets open autopsy.
Type sudo autopsy and leave the terminal open. Open your browser and type http://localhost:9999/autopsy and you will see autopsy front page.
Obviously click "new case" button and fill all the information.
Then add host.
After that add your image
Enter image path. For example my image was in /home/this/honeynet/honeynet/honeypot.hda8.dd
Select Volume!
Then just add.
All preparations done. Now click analyze to begin.
How to recover deleted files
cd to your honeynet folder where the image file is stored. Then create two new folders
mkdir allocated deleted
Then type
tsk_recover -a honeypot.hda8.dd allocated/
tsk_recover honeypot.hda8.dd deleted/
As you can see it recovered some files.
Good tutorial for terminal file recovery:
"If you are doing forensic analysis, be careful: never run files that could be hostile."
"If you are doing forensic analysis with potentially hostile software,
don’t use production machines or computers with sensitive information."
So what we know about the image ?
You have download the / partition of a compromised RH 6.2
Linux box. Your mission is to recover the deleted rootkitfrom the / partition. Below are a list of all the partitions
that made up the compromised system.
/dev/hda8 / <----- The partition you downloaded
/dev/hda1 /boot
/dev/hda6 /home
/dev/hda5 /usr
/dev/hda7 /var
/dev/hda9 swap
I opened my autopsy and noticed right away from the front page two deleted files.
The .tgz file was interesting so I decided to untar it.
last/
It created a folder named last. As you can see from the picture above, there is a folder named last which is deleted. I started to look what kind of files it contained because I managed to recover the folder from tar file.
It contained files for ssh and file named linsniffer which is very suspicious. If you look files, modified date from properties, we can see these are created before 15 March. 2001 when the rootkit was deleted.
The install file was very interesting. I opened it with nano
nano install
And it revealed something very interesting =) Then I googled the linsniffer because sniffing sounds so suspicious. What is linsniffer ? returned: Powerful Linux ethernet sniffer
"linsniffer is an ethernet sniffer. It sits and listens on a network
and grabs every packet it sees. This is why ssh is a good thing…"
So it seems the sniffer was part of the rootkit and from install packet which is image above we can see clearly a text saying: Rootkitului so I can almost clearly say this is the rootkit.
Then I looked a little bit the sshd config file:
It has been set to accept empty passwords. If this machine were production server it would absolutely not accept empty passwords if it has been set up right!
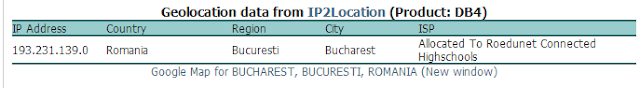
IP address
The install file included some IP addresses. I then put them into IP location finder http://www.iplocation.net/index.php and the IP pointed to Romania so we can suspect that the rootkit came from there unless it was installed through proxy server.
And then to the questions from Scan of the month:
1. Show step by step how you identify and recover the deleted rootkit
from the / partition.
2. What files make up the deleted rootkit?
All files that were under /last folder.
Bonus Question:
Was the rootkit ever actually installed on the system?
How do you know?
Will see if I have time to solve this. But I know it can be solved.















Ei kommentteja:
Lähetä kommentti