Our homework was to create three error messages and then analyze errors from log files.
SSH-"error"
My first error is not really error, but anyway I installed openssh-server and tried to login without password. Of course that would fail.
Then I started searching ssh logs from /var/log but didn't find anything useful so I did a search
grep -ir ssh /var/log/*
where:
grep = print lines matching a pattern
i = Ignore case distinctions in both the PATTERN and the input files.
r = Read all files under each directory, recursively
(http://explainshell.com/explain?cmd=grep+-ir)
And that revealed the path I should be looking /var/log/auth.log
However everything can be seen from the search so no point opening that file. It clearly says: Failed password for this from 127.0.0.1 port 58216 and so on...
Then my second error is what I came up with the class during apache php installation for all users. (http://nikinlinux.blogspot.fi/2013/04/user-homepages-on-apache.html)
From the part where I have to edit this file "sudoedit php5.conf" I somehow failed editing the file and now my apache won't restart.
This time I knew the apache2 log file would be under /var/log/apache2 and from there I chose error.log. It didn't reveal anything useful but as you can see from the image above the error message is very clear and I don't need to look log files. There is on </IfModule> without matching start point and when I look my php5.conf file again I noticed I forgot to comment out the last IfModule
One comment there # and sudo service apache2 restart works again!
Third problem: I commented out all cdrom lines from /etc/apt/sources.list file and it is saying failed to fetch cdrom source. It is very clear and I just could remove the cdrom lines from apt because I don't use it.
Once I also encountered dpkg lock error:
This means some other program might be using apt-get. For example if you have package manager open and forget to use sudo before apt-get you can get this error message. You can get this error from other reasons too and to fix that type: sudo rm -fv /var/lib/dpkg/lock to remove the lock and continue using apt-get normally.
I found some log files under /var/log/dpkg.log and /var/log/apt/ history.log and term.log these were not much help because I had to google the answer how to remove lock.
This page is a random collection of notes addressed to myself. Nothing here is intended as a guide per say, however i have posted them hoping that it may help someone. Blog about Linux and unix related stuff. Everything in this blog can be copied or edited GNU General Public License (version 2 or newer) http://www.gnu.org/licenses/gpl.html
keskiviikko 25. syyskuuta 2013
How To Set Up Apache Virtual Hosts
About virtual hosts
Virtual hosting is a method for hosting multiple domain names (with separate handling of each name) on a single server (or pool of servers). This allows one server to share its resources, such as memory and processor cycles, without requiring all services provided to use the same host name.
For example you have one computer which runs apache. Then you set three websites there: test1.com test2.com test3.com and all of the pages can be accessed from Iternet even though the computer has one IP address.
Set Up
First install apache2
sudo apt-get install apache2
Create new folder where you want to host your pages for example (where -P creates automatically all the parent folders):
sudo mkdir -p /var/www/sivusto1/public_html
(This step is not mandatory if you for example run pages from user home directory.)
Grant user ownership to the folder
sudo chown -R $USER:$USER /var/www/sivusto1/public_html
Make sure everyone can read your new files
sudo chmod -R 755 /var/www
(Continue from here)
Create new index.html under public_html
sudoedit /var/www/sivusto1/public_html/index.html
Add some test html to the index file
Here I have created two virtual host pages.
Create new virtual host file
sudo cp /etc/apache2/sites-available/default /etc/apache2/sites-available/sivusto1.com
Turn on virtual hosts
sudoedit /etc/apache2/sites-available/sivusto1.com
Edit the file like this. ServerAdmin for example your name or email, ServerName is the address of your page and ServerAlias is of course alias address, you can add multiple aliases.
<VirtualHost *:80>
ServerAdmin webmaster@sivusto1.com
ServerName sivusto1.com
ServerAlias www.sivusto1.com
From below set the document root:
DocumentRoot /var/www/sivusto1/public_html
Then save and exit nano.
Activate your new host
sudo a2ensite sivusto1.com
to disable host: sudo a2dissite sivusto1.com
Restart your server
sudo service apache2 restart
You may see and error log during restarting, but it's nothing to worry about
Set up your local hosts (This step is for testing purposes only. It mimics the DNS search and should not be applied in production server)
Open your hosts file with:
sudoedit /etc/hosts
And create lines:
#Virtual Hosts
computeriphere sivusto1.com
computeriphere www.sivusto1.com
Save and exit nano. Now it's time to try your site. Open browser and type either sivusto1.com or www.sivusto1.com and your page will load!
Original instructions: https://www.digitalocean.com/community/articles/how-to-set-up-apache-virtual-hosts-on-ubuntu-12-04-lts
Questions: Can I insert all the pages to the default file and not duplicate it every time ? Answer: probably yes, but it is easier to maintain available sites with different files.
My personal virtualhost setting with Varnish:
<VirtualHost *:8080>
ServerAdmin niki.ahlskog@gmail.com
ServerName nikiahlskog.com
ServerAlias www.nikiahlskog.com
DocumentRoot /home/niki/public_html/
<Directory />
Options FollowSymLinks
AllowOverride All
</Directory>
<Directory /home/niki/public_html/>
Options Indexes FollowSymLinks
AllowOverride All
Order allow,deny
allow from all
</Directory>
</VirtualHost>
Other example:
<VirtualHost *:8080>
ServerAdmin niki.ahlskog@gmail.com
ServerName nikiahlskog.com
ServerAlias www.nikiahlskog.com
DocumentRoot /home/niki/public_html/
<Directory /home/niki/public_html/folder/>
Options Indexes FollowSymLinks
AllowOverride All
Order allow,deny
Allow from all
</Directory>
</VirtualHost>
Virtual hosting is a method for hosting multiple domain names (with separate handling of each name) on a single server (or pool of servers). This allows one server to share its resources, such as memory and processor cycles, without requiring all services provided to use the same host name.
For example you have one computer which runs apache. Then you set three websites there: test1.com test2.com test3.com and all of the pages can be accessed from Iternet even though the computer has one IP address.
Set Up
First install apache2
sudo apt-get install apache2
Create new folder where you want to host your pages for example (where -P creates automatically all the parent folders):
sudo mkdir -p /var/www/sivusto1/public_html
(This step is not mandatory if you for example run pages from user home directory.)
Grant user ownership to the folder
sudo chown -R $USER:$USER /var/www/sivusto1/public_html
Make sure everyone can read your new files
sudo chmod -R 755 /var/www
(Continue from here)
Create new index.html under public_html
sudoedit /var/www/sivusto1/public_html/index.html
Add some test html to the index file
<html>
<head>
<title>www.sivusto1.com</title>
</head>
<body>
<h1>Success: You Have Set Up a Virtual Host one!</h1>
</body>
</html>
Save and exit (CTRL + O and CTRL + X)
Here I have created two virtual host pages.
Create new virtual host file
sudo cp /etc/apache2/sites-available/default /etc/apache2/sites-available/sivusto1.com
Turn on virtual hosts
sudoedit /etc/apache2/sites-available/sivusto1.com
Edit the file like this. ServerAdmin for example your name or email, ServerName is the address of your page and ServerAlias is of course alias address, you can add multiple aliases.
<VirtualHost *:80>
ServerAdmin webmaster@sivusto1.com
ServerName sivusto1.com
ServerAlias www.sivusto1.com
From below set the document root:
DocumentRoot /var/www/sivusto1/public_html
Then save and exit nano.
Activate your new host
sudo a2ensite sivusto1.com
to disable host: sudo a2dissite sivusto1.com
Restart your server
sudo service apache2 restart
You may see and error log during restarting, but it's nothing to worry about
Set up your local hosts (This step is for testing purposes only. It mimics the DNS search and should not be applied in production server)
Open your hosts file with:
sudoedit /etc/hosts
And create lines:
#Virtual Hosts
computeriphere sivusto1.com
computeriphere www.sivusto1.com
Save and exit nano. Now it's time to try your site. Open browser and type either sivusto1.com or www.sivusto1.com and your page will load!
Original instructions: https://www.digitalocean.com/community/articles/how-to-set-up-apache-virtual-hosts-on-ubuntu-12-04-lts
Questions: Can I insert all the pages to the default file and not duplicate it every time ? Answer: probably yes, but it is easier to maintain available sites with different files.
My personal virtualhost setting with Varnish:
<VirtualHost *:8080>
ServerAdmin niki.ahlskog@gmail.com
ServerName nikiahlskog.com
ServerAlias www.nikiahlskog.com
DocumentRoot /home/niki/public_html/
<Directory />
Options FollowSymLinks
AllowOverride All
</Directory>
<Directory /home/niki/public_html/>
Options Indexes FollowSymLinks
AllowOverride All
Order allow,deny
allow from all
</Directory>
</VirtualHost>
Other example:
<VirtualHost *:8080>
ServerAdmin niki.ahlskog@gmail.com
ServerName nikiahlskog.com
ServerAlias www.nikiahlskog.com
DocumentRoot /home/niki/public_html/
<Directory /home/niki/public_html/folder/>
Options Indexes FollowSymLinks
AllowOverride All
Order allow,deny
Allow from all
</Directory>
</VirtualHost>
lauantai 21. syyskuuta 2013
Setting Up Raspberry Pi Server
I wanted to re install my Raspberry Pi. http://nikinlinux.blogspot.fi/2013/03/raspberry-pi-credit-card-sized-computer.html
First go to:
First go to:
http://www.raspberrypi.org/downloads
And download Raspbian Image 2013-09-10-wheezy-raspbian.zip
And download Raspbian Image 2013-09-10-wheezy-raspbian.zip
Download also Win32DiskImager from the same site. Extract the Win32DiskImager somewhere on your computer for example Desktop.
Insert your memory card into computer.
Open the DiskImager software, press the icon that looks like a folder and search for your raspbian image. Also check that the device is pointing to your memory card. Click write.
After the file is writed click OK and insert it to your raspberry Pi. Then plug in all the cables and power plug at last. It should boot up and show you the raspberry pi config window.
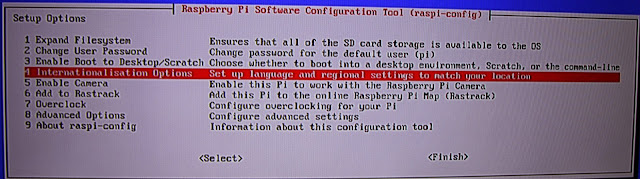
1. First select Expand Filesystem if you want to use whole memory card as disk space and often people do. The space is created after next reboot.
2. If you want to change the PI account default password select this. Default password is raspberry
4. Select keyboard layout from here and system time settings.
7. Overclocking is a new tool, you can overclock your raspberry pi and it is so simple check it out!
8. Then go to advanced options if you are going to use raspberry pi as a server, otherwise you are ready and can skip few next steps.
From advanced options it is good to set up hostname for your server. It sets the visible name for PI on your local network (A2).
(A3) Memory split, with this option you can select how much memory is dedicated to the GPU if you are using the graphical user interface you should give it as much memory as possible. We are going to set up a server so I'm going to use only command line and therefore I set up it as low as possible, in this case 16mb.
(A4) SSH, if you want to acces your server from other computer you have to turn this on. We are going to configure our server from windows computer so set this on.
Now you are finished. Go back and finish. If it doesn't reboot just pull the plug off the PI and in again.
Now it should show you the raspberry pi terminal:
Just to make sure type service ssh status to see if the service has started.
Then check your IP address by typing ifconfig
Look for a line which says: inet addr: write down the ip after that. It's the IP your router has given to PI.
Then you can pull off all the cables but power and ethernet. Your PI is ready to be configured from other computer. However if you would like to use the graphical environment type startx in the terminal window and it should load.
Go to your windows computer and download putty.exe http://www.chiark.greenend.org.uk/~sgtatham/putty/download.html
In putty window type your PI ip address we just looked before and leave port 22. Then connect.
Pi should ask your password and after you have entered it you should see the welcome message
Security
Now we want to make our server as secure as possible. Lets add a new user and delete the default PI account.
type sudo useradd -m accountname where "accountname" is your account name.
Set password for your account type: sudo passwd accountname
Now lets add our new account to same groups as PI. type sudoedit /etc/group
Go through the file adding your account ,accountname to the end of all the groups that pi is in. For example my account name is shnigi.
When you are ready press CTRL + O to save, press enter and then CTRL + X to quit nano. All nano command are visible in the bottom of the terminal screen. Mark ^ means CTRL + letter. Of course if you just want to add other user in PI you don't need to go through this file. Now type exit and try to log in your other account. It should give you the welcome message again.
Next set the default shell for your new account when you have logged in with it. Type:
chsh -s /bin/bash
After this you could delete the PI account if it is no longer required. Of course there are also a lot of other aspects to make PI more secure.
Setting up the networking
Next step is to give the Raspberry Pi an static IP address. This is a little more complex as it depends upon your own setup and router. How to configure your router I suggest you to check: http://portforward.com/ for more information. This article is only about Raspberry Pi.
If you again type ifconfig to the terminal it will show your address in eth0
Also check your router address by typing route
To change to static IP address type
cd /etc/network
sudo nano interfaces
replace the line "iface eth0 inet dhcp" like in this picture. Of course use your addresses from the earlier steps we just did.
CTRL + O to save CTRL + X to exit nano. Next type cd .. and nano resolv.conf to make sure your nameserver is set up correctly.
Next it is good idea to reboot the pi with sudo reboot wait few minutes and connect again with putty. After logging in check using ifconfig to confirm that you have a static IP address. All done. Now just set up your router and start installing LAMP for example.
start by updating repositories:
sudo apt-get update
Install apache web server
sudo apt-get install apache2
Install MySQL server
sudo apt-get install mysql-server
during the installation mysql asks to set root password.
Perl is installed as part of the operating system so just add php.
sudo apt-get install php5
sudo apt-get install php5-mysql
LAMP stack is now installed. You can check if you see the apache welcome page by pointing your browser to PI's IP address.
Next we are going to install phpmyadmin graphical user interface for MySQL
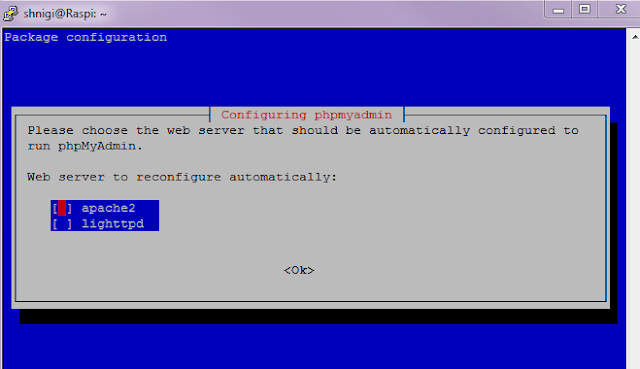
sudo apt-get install phpmyadmin
it will ask web server to configure, select apache2. It will also ask to create database, select yes.
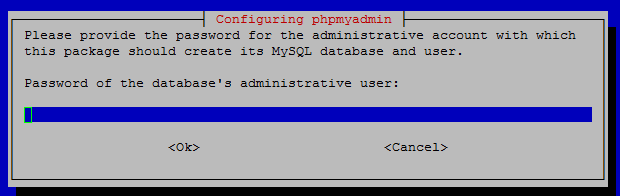
Set phpmyadmin password.
Create a symbolic link for phpmyadmin to be accessed from the internet. If you want more secure server skip this step. Phpmyadmin propably has some sort or risks and it is always more secure to use it locally.
sudo ln -s /usr/share/phpmyadmin/ /var/www/phpmyadmin
Then restart apache to take changes
sudo service apache2 restart
type http://yourPi-IP/phpmyadmin to acces your phpmyadmin
sudo apt-get install php5
sudo apt-get install php5-mysql
LAMP stack is now installed. You can check if you see the apache welcome page by pointing your browser to PI's IP address.
sudo apt-get install phpmyadmin
it will ask web server to configure, select apache2. It will also ask to create database, select yes.
Set phpmyadmin password.
Create a symbolic link for phpmyadmin to be accessed from the internet. If you want more secure server skip this step. Phpmyadmin propably has some sort or risks and it is always more secure to use it locally.
sudo ln -s /usr/share/phpmyadmin/ /var/www/phpmyadmin
Then restart apache to take changes
sudo service apache2 restart
type http://yourPi-IP/phpmyadmin to acces your phpmyadmin
Test if php is working:
sudoedit /var/www/index.php
Insert this code:
<html>
<head>
<title>PHP Test</title>
</head>
<body>
<?php echo '<p>Hello World</p>'; ?>
</body>
</html>
Save and quit nano. Type to your browser: localhost/index.php
If you see this, it works:
tiistai 17. syyskuuta 2013
Metapackages (HowTo) Packagin a script and about apt-get
This time we are going to install multiple programs with apt-get and create a metapackage (.deb) file. To create a .deb file you will need at least two programs, but we are going to use three. The third one is for checking the package.
To update repositories and install all the tools with single command type this to terminal:
sudo apt-get update && sudo apt-get -y install equivs lintian gdebi
GDebi is a tool that can install .deb packages. It is available with a graphical interface, but also has a command line option.
Lintian checks Debian software packages for common inconsistencies and errors.
Equivs is a dummy package which can be used to create Debian packages, which only contain dependency information. This way, you can make the Debian package management system believe that equivalents to packages on which other packages do depend on are actually installed.
First we are going to create that dummy file for our .deb
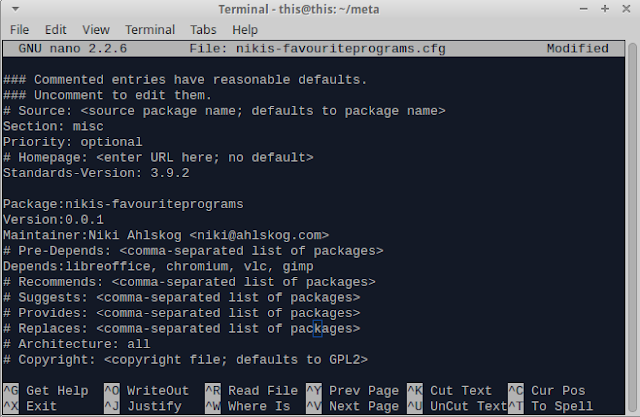
equivs-control nikis-favouriteprograms.cfg
(replace nikis-favouriteprograms with your own package name. It has to be unique.)
open it with nano for example.
nano nikis-favouriteprograms.cfg
Edit at least these lines and remember to remove # comment mark from the start:
Package with your package name without .cfg
Version add it like 0.0.1 and remember, you can never go back with the version number !
Maintainer Enter your name or who ever is going to maintain the package, also email address
Depends Here you can enter the depends, for example apache2, nmon etc...
Like this:
CTRL + O to save, press enter and CTRL + X to exit.
Then time to build your package:
equivs-build nikis-favouriteprograms.cfg
Next try your package with Lintian.
lintian nikis-favouriteprograms_0.0.1_all.deb
if terminal gives no warnings and returns new empty line your package is fine.
Next install your package.
sudo gdebi -n nikis-favouriteprograms_0.0.1_all.deb
Your package should install and you can pat yourself on the shoulder.
Notice: my package couldn't install first because chromium was chromium-browser.
Original instructions: http://terokarvinen.com/2011/create-deb-metapackage-in-5-minutes
Wrapping a script in .deb file
Do the same steps as before but create a shell script for example which you want to pack. For example http://nikinlinux.blogspot.fi/2013/08/creating-shell-script.html
Put the script in the same folder as the .cfg.
Give your shellscript execute permissions chmod 755 mystatus.sh
Then edit the cfg file a little bit, you can leave depencies blank if you want, remove the comment from option "File" and after that enter your shellscript name, one space and path to install for example /home.
Then build your package and install it to see if it is working. Mine worked.
To update repositories and install all the tools with single command type this to terminal:
sudo apt-get update && sudo apt-get -y install equivs lintian gdebi
GDebi is a tool that can install .deb packages. It is available with a graphical interface, but also has a command line option.
Lintian checks Debian software packages for common inconsistencies and errors.
Equivs is a dummy package which can be used to create Debian packages, which only contain dependency information. This way, you can make the Debian package management system believe that equivalents to packages on which other packages do depend on are actually installed.
First we are going to create that dummy file for our .deb
equivs-control nikis-favouriteprograms.cfg
(replace nikis-favouriteprograms with your own package name. It has to be unique.)
open it with nano for example.
nano nikis-favouriteprograms.cfg
Edit at least these lines and remember to remove # comment mark from the start:
Package with your package name without .cfg
Version add it like 0.0.1 and remember, you can never go back with the version number !
Maintainer Enter your name or who ever is going to maintain the package, also email address
Depends Here you can enter the depends, for example apache2, nmon etc...
Like this:
CTRL + O to save, press enter and CTRL + X to exit.
Then time to build your package:
equivs-build nikis-favouriteprograms.cfg
Next try your package with Lintian.
lintian nikis-favouriteprograms_0.0.1_all.deb
if terminal gives no warnings and returns new empty line your package is fine.
Next install your package.
sudo gdebi -n nikis-favouriteprograms_0.0.1_all.deb
Your package should install and you can pat yourself on the shoulder.
Notice: my package couldn't install first because chromium was chromium-browser.
Original instructions: http://terokarvinen.com/2011/create-deb-metapackage-in-5-minutes
Wrapping a script in .deb file
Do the same steps as before but create a shell script for example which you want to pack. For example http://nikinlinux.blogspot.fi/2013/08/creating-shell-script.html
Put the script in the same folder as the .cfg.
Give your shellscript execute permissions chmod 755 mystatus.sh
Then edit the cfg file a little bit, you can leave depencies blank if you want, remove the comment from option "File" and after that enter your shellscript name, one space and path to install for example /home.
Then build your package and install it to see if it is working. Mine worked.
perjantai 13. syyskuuta 2013
Criminals and good citizens - Scan Of The Month 15 (How To Recover Deleted Files)
Our hometask was to download Scan of the month 15 and recover deleted rootkit from the / partition
Source: http://old.honeynet.org/scans/scan15/
Lets start.
Open up terminal and type
sudo apt-get update
then copy the download link from honeynet or just download it from there. However I used
wget http://old.honeynet.org/scans/scan15/honeynet.tar.gz
I downloaded it in to my home folder and then untarred it with
tar -xvf honeynet.tar.gz
where -x = Extract files from an archive
-v = verbosely list files processed
-f = use archive file or device archive
SUMMARY
-------
You have download the / partition of a compromised RH 6.2
Linux box. Your mission is to recover the deleted rootkit
from the / partition.
What is rootkit actually ?
From Wikipedia: " rootkit is a stealthy type of software, often malicious, designed to hide the existence of certain processes or programs from normal methods of detection and enable continued privileged access to a computer"
So basically rootkit is not a virus which sabotages your computer. Its basic idea is to hide itself from users and give root access to someone else who then can steal your documents or somehow make changes to the system. It is a "kit" which contain files to give "root" access to the marauder.
then I downloaded autopsy to do the forensics
sudo apt-get install autopsy
What is autopsy ?
http://www.sleuthkit.org/
"Autopsy™ is a digital forensics platform and graphical interface to The Sleuth Kit™ and other digital forensics tools. It can be used by law enforcement, military, and corporate examiners to investigate what happened on a computer. You can even use it to recover photos from your camera's memory card."
from the / partition. Below are a list of all the partitions
that made up the compromised system.
/dev/hda8 / <----- The partition you downloaded
/dev/hda1 /boot
/dev/hda6 /home
/dev/hda5 /usr
/dev/hda7 /var
/dev/hda9 swap
this@this:~/honeynet/honeynet/deleted$ tar -xvf lk.tgz
last/
It created a folder named last. As you can see from the picture above, there is a folder named last which is deleted. I started to look what kind of files it contained because I managed to recover the folder from tar file.
Use autopsy / sleuthkit to see what files have been deleted from / and then recover them with terminal commands.
2. What files make up the deleted rootkit?
All files that were under /last folder.
Bonus Question:
Was the rootkit ever actually installed on the system?
How do you know?
Will see if I have time to solve this. But I know it can be solved.
On 15 March. 2001, a Linux honeypot
was successfully compromised, a rootkit was download to the / partition
and then deleted from the system. Your mission is to find and recover the deleted rootkit.
If you are not sure where to begin on conducting this forensic analysis
and recover the rootkit, we highly reccommend you start with the Forensic Challenge.
The steps you will have to follow for the rootkit recovery are similar
to the steps discussed there. We have posted only the / partion for
download to keep this challenge simple. The compressed image is 13MB, (honeynet.tar.gz) MD5=0dff8fb9fe022ea80d8f1a4e4ae33e21.
Once you have downloaded, untarred, and unzipped the partition image,
it will be 255 MB and the checksum should be
MD5=5a8ebf5725b15e563c825be85f2f852e.
- Show step by step how you identify and recover the deleted rootkit from the / partition.
- What files make up the deleted rootkit?
Bonus Question:
Was the rootkit ever actually installed on the system? How do you know?
Was the rootkit ever actually installed on the system? How do you know?
Source: http://old.honeynet.org/scans/scan15/
Lets start.
Open up terminal and type
sudo apt-get update
then copy the download link from honeynet or just download it from there. However I used
wget http://old.honeynet.org/scans/scan15/honeynet.tar.gz
I downloaded it in to my home folder and then untarred it with
tar -xvf honeynet.tar.gz
where -x = Extract files from an archive
-v = verbosely list files processed
-f = use archive file or device archive
SUMMARY
-------
You have download the / partition of a compromised RH 6.2
Linux box. Your mission is to recover the deleted rootkit
from the / partition.
What is rootkit actually ?
From Wikipedia: " rootkit is a stealthy type of software, often malicious, designed to hide the existence of certain processes or programs from normal methods of detection and enable continued privileged access to a computer"
So basically rootkit is not a virus which sabotages your computer. Its basic idea is to hide itself from users and give root access to someone else who then can steal your documents or somehow make changes to the system. It is a "kit" which contain files to give "root" access to the marauder.
then I downloaded autopsy to do the forensics
sudo apt-get install autopsy
What is autopsy ?
http://www.sleuthkit.org/
"Autopsy™ is a digital forensics platform and graphical interface to The Sleuth Kit™ and other digital forensics tools. It can be used by law enforcement, military, and corporate examiners to investigate what happened on a computer. You can even use it to recover photos from your camera's memory card."
This is what I have so far done. Now lets open autopsy.
Type sudo autopsy and leave the terminal open. Open your browser and type http://localhost:9999/autopsy and you will see autopsy front page.
Obviously click "new case" button and fill all the information.
Then add host.
After that add your image
Enter image path. For example my image was in /home/this/honeynet/honeynet/honeypot.hda8.dd
Select Volume!
Then just add.
All preparations done. Now click analyze to begin.
How to recover deleted files
cd to your honeynet folder where the image file is stored. Then create two new folders
mkdir allocated deleted
Then type
tsk_recover -a honeypot.hda8.dd allocated/
tsk_recover honeypot.hda8.dd deleted/
As you can see it recovered some files.
Good tutorial for terminal file recovery:
"If you are doing forensic analysis, be careful: never run files that could be hostile."
"If you are doing forensic analysis with potentially hostile software,
don’t use production machines or computers with sensitive information."
So what we know about the image ?
You have download the / partition of a compromised RH 6.2
Linux box. Your mission is to recover the deleted rootkitfrom the / partition. Below are a list of all the partitions
that made up the compromised system.
/dev/hda8 / <----- The partition you downloaded
/dev/hda1 /boot
/dev/hda6 /home
/dev/hda5 /usr
/dev/hda7 /var
/dev/hda9 swap
I opened my autopsy and noticed right away from the front page two deleted files.
The .tgz file was interesting so I decided to untar it.
last/
It created a folder named last. As you can see from the picture above, there is a folder named last which is deleted. I started to look what kind of files it contained because I managed to recover the folder from tar file.
It contained files for ssh and file named linsniffer which is very suspicious. If you look files, modified date from properties, we can see these are created before 15 March. 2001 when the rootkit was deleted.
The install file was very interesting. I opened it with nano
nano install
And it revealed something very interesting =) Then I googled the linsniffer because sniffing sounds so suspicious. What is linsniffer ? returned: Powerful Linux ethernet sniffer
"linsniffer is an ethernet sniffer. It sits and listens on a network
and grabs every packet it sees. This is why ssh is a good thing…"
So it seems the sniffer was part of the rootkit and from install packet which is image above we can see clearly a text saying: Rootkitului so I can almost clearly say this is the rootkit.
Then I looked a little bit the sshd config file:
It has been set to accept empty passwords. If this machine were production server it would absolutely not accept empty passwords if it has been set up right!
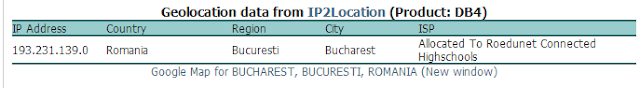
IP address
The install file included some IP addresses. I then put them into IP location finder http://www.iplocation.net/index.php and the IP pointed to Romania so we can suspect that the rootkit came from there unless it was installed through proxy server.
And then to the questions from Scan of the month:
1. Show step by step how you identify and recover the deleted rootkit
from the / partition.
2. What files make up the deleted rootkit?
All files that were under /last folder.
Bonus Question:
Was the rootkit ever actually installed on the system?
How do you know?
Will see if I have time to solve this. But I know it can be solved.
Tilaa:
Blogitekstit (Atom)